 Can you be traced from your email? The answer is yes. Tracing an individual’s whereabouts through their email address can be daunting, but it is possible. Email addresses may not explicitly reveal personal identifying information. But techniques are available to extract additional details about the individual associated with an email address.
Can you be traced from your email? The answer is yes. Tracing an individual’s whereabouts through their email address can be daunting, but it is possible. Email addresses may not explicitly reveal personal identifying information. But techniques are available to extract additional details about the individual associated with an email address.
It is vital to evaluate the features, terms of service, and privacy policies of anonymous email providers before utilizing their services to verify that they fulfill your unique requirements for maintaining your anonymity and security.
What is email tracking?
Email tracking is a method that enables senders to track the delivery and engagement of their emails. It entails inserting tracking codes or pixels in emails to collect data when recipients open or interact with them. This information assists senders in tracking email opens, link clicks, and other analytics, which provides insights into recipient behavior and campaign efficacy.
Tracking email can track if the recipient opens the email, how often they open it, and if they visit any links within the email, providing insights into their behavior. Advanced tracking methods can also collect more specific data, such as engagement length, user-agent details, and geolocation tracking.
Senders often utilize specialist email marketing software or services that offer tracking capability to enable email tracking. Based on the information gathered, these systems create personalized tracking pixels for each receiver and generate analytics reports.
How does email tracking work?
Email tracking works by inserting a short tracking code or pixel into the email’s content. When the receiver opens the email, the tracking code is activated, allowing the sender to collect data about the recipient’s interaction. This usually entails tracking the open email event and tracking clicks on links within the email. The tracking code transmits signals back to the sender’s server, storing pertinent data such as the opening time, IP address, and link click details. This information can create reports and analytics that provide insights into engagement with emails and efficacy. Email tracking is subject to the recipient’s email client settings and privacy preferences. Some recipients may choose to reject or turn off email tracking for privacy concerns.
You can also read: Can You Get a Computer Virus by Opening an Email?
Can you be traced from your email?
Even while an email address in and of itself does not give any personally identifiable information, several methods and criteria can track down an individual. These include searching for IP addresses in the email header. Also included are utilizing information linked with associated accounts, investigating metadata and content, and enlisting the support of legal processes and subject matter experts. On the other hand, it is essential to remember that ordinary people and illegal entities often have limited resources to track down someone based only on their email address.
How do anonymous email accounts work?
Anonymity can be maintained through anonymous email accounts, allowing users to send and receive electronic correspondence without revealing their identities. The use of these accounts is made possible by the use of several safeguards designed to preserve the user’s confidentiality. The following is a brief review of the regular operation of anonymous email accounts:
- The user must not submit personal identifying information such as their name, address, or phone number while creating an anonymous email account. To remain anonymous, they can use pseudonyms or makeup details.
- Anonymous email companies frequently prioritize user privacy and use encryption technology to secure email content to prevent illegal access and eavesdropping.
- Anonymous email services may conceal the user’s IP address by routing emails through proxy servers or employing unknown techniques like Tor.
- Some providers provide email forwarding, which includes sending emails through different servers or accounts, making tracing the original sender difficult.
- Anonymous email services may have policies limiting the retention of user data, lowering the likelihood of saved information potentially connected to the user’s identity.
How can I send an anonymous email without being traced?
You will need to protect both your identity and your anonymity by taking a number of steps before sending an anonymous email so that it is not traceable back to you.
While total confidentiality is impossible to accomplish, the following are some broad steps you can take to increase your privacy:
1. Create a new email account
To retain online privacy, many people use a new email account. Individuals can avoid revealing their true identity by creating a new account and using pseudonyms or irrelevant aliases. Selecting an email service provider that values privacy and does not require personal information during the signup process is critical. This reduces the possibility of being tracked back to the reverse email account.
2. Use a “burner” email
Another option to remain anonymous is to use a “burner” email. A burner email is a temporary or disposable email address used for a specific purpose or a limited period. Users can create these accounts rapidly without revealing personal identifying information and then abandon them, limiting the possibility of being traceable back to the user. Burner emails might be handy when participating in activities that demand concise communication while maintaining anonymity.
3. Use an encrypted email
Using an encrypted email service is an excellent approach to keeping your identity hidden and your correspondence secure. Encrypted email services use encryption techniques to safeguard the content of your emails, guaranteeing that only the intended recipient can decrypt and read them. End-to-end encryption prevents even the email service provider from accessing the message contents. This considerably lowers the possibility of illegal access or interception of important information, protecting your anonymity.
4. Use a VPN
Using a VPN (Virtual Private Network) to retain anonymity and secure your online privacy is an efficient strategy. A VPN connects your device to the internet in a secure and encrypted manner by routing your internet traffic through a remote server managed by the VPN service provider. It conceals your IP address and encrypts your data in this way, making it harder for others to link your online actions to your true identity. The VPN server operates as a middleman, making your internet traffic appear to originate from a different location. This helps to secure your anonymity and offers another layer of defense against efforts at surveillance or monitoring.
You may also like: Gmail vs Outlook: Which One is Safer?
Anonymous email providers you can use
Here are some examples of anonymous email providers that you can use to protect your privacy and anonymity.
1. ProtonMail
ProtonMail is a privacy and security-focused encrypted email service. End-to-end encryption ensures that even ProtonMail cannot access your communications because the content of your emails is encrypted on your device and can only be decodable by the intended receiver. ProtonMail is in Switzerland, which has strict data protection and privacy laws.
Key Features:
- Signing up requires no personal information, and you can create an anonymous email account without disclosing your identity
- Includes features such as self-destructing emails, which let you choose an expiration time for your emails, which adds an added degree of secrecy
- Offers an easy-to-use interface and is provided as a webmail service as well as iOS and Android mobile apps
- Includes advanced security features such as two-factor authentication (2FA), encrypted contacts, and the ability for non-ProtonMail users to add password-protected emails
2. CounterMail
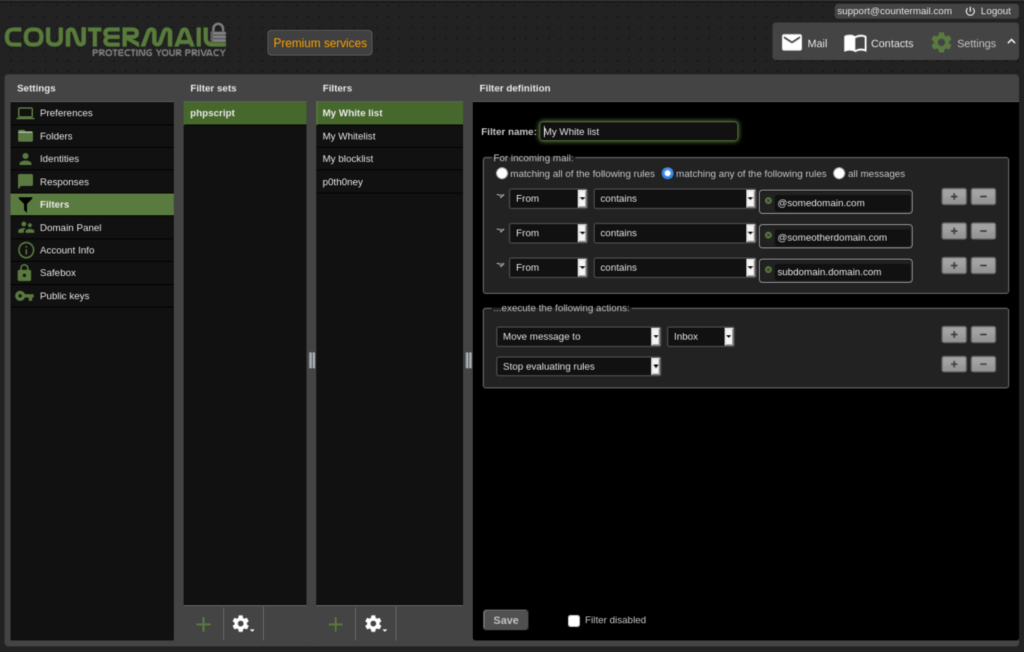
CounterMail is a secure email service that stresses privacy and security. End-to-end encryption is provided, which means that your emails are encrypted on your device and can be decodable by the intended receiver. CounterMail wants to safeguard your emails against eavesdropping and illegal access.
Key Features:
- All data, including email metadata and account information, is stored on secured hard drives separate from the server through its diskless web server
- Has built-in support for OpenPGP encryption and anonymous email headers, which eliminate potentially identifying information from email headers
- Features multi-factor authentication (MFA) for greater security and supports USB key login, which adds an extra degree of protection to your account access
- Includes a secure email client that you can download and install on your PC
3. Tutanota
Tutanota is an email service that encrypts messages and places a premium on users’ privacy and safety. It provides end-to-end encryption, which ensures that the content of your emails may only be viewed by the person for whom they are meant to be. Because of this, even Tutanota cannot read your messages because the encrypting and decrypting processes occur on your device.
Key Features:
- Lets you register without giving your name or phone number
- User-friendly webmail interface and mobile apps for iOS and Android
- Offers functions like calendar integration, safe file storage, and contacts that are protected
- Employs extra security precautions, such as two-factor authentication (2FA) support and phishing attack defenses
4. AnonAddy
AnonAddy is an anonymous email forwarding service that aids in maintaining your anonymity and protecting your privacy. You can use it to make one-time use email accounts, commonly referred to as aliases, that you can use to send and receive emails without giving away your actual email address.
Key Features:
- It lets you create unique email aliases that forward to your actual address
- Supports custom domains for aliases by setting up email filters, allowing listing or blocklisting senders, and forwarding emails to numerous addresses
- Offers a browser extension to generate and manage aliases without visiting the website
- Masks your email address but does not encrypt or store emails
5. Mailfence
Mailfence is a secure email service offering private and fast communication. It provides end-to-end encryption, which means that the content of your emails is encrypted on your device and can be decoded only by the intended recipient. This assures that not even Mailfence has access to your communications.
Key Features:
- Offers a range of security features, including two-factor authentication (2FA), digital signatures, and encryption for email attachments
- Provides a secure calendar, document storage, and collaboration tools to enhance productivity while maintaining privacy
- Supports the use of PGP (Pretty Good Privacy) encryption, allowing you to send and receive encrypted messages with users outside of the Mailfence ecosystem
- Provides a user-friendly web interface and supports access via mobile devices and social media using standard email protocols
- Allows custom domain usage, enabling businesses and organizations to use their domain names for email addresses
Also read: Our Top Picks: 15 Most Secure Email Providers
Our Verdict: Can you be traced from your email?
Although it can be difficult, tracing someone directly through their email is possible. Several variables influence the extent of traceability, such as the steps you take to safeguard your anonymity and the sophistication used by those seeking to find you.
When using a standard email account, email servers may record your IP address and connect it to your online activities. However, linking that IP address to your unique identity might take extra resources, including assistance from internet service providers or legal action.
Anonymous or encrypted email services, along with other anonymity tools like VPNs and Tor, can significantly lower the likelihood of identifying someone through email. These services offer extra security layers. Making it harder for outsiders to trace your identity or keep tabs on your online actions.
It’s crucial to remember that while maintaining anonymity is possible, no technique can ensure complete security. Furthermore, we advise you to speak with specialists in internet security and privacy or legal experts familiar with the relevant jurisdiction if you are worried about your privacy and anonymity.