 The end-to-end encryption that ProtonMail provides and the company’s dedication to protecting user privacy helped the company gain popularity. Despite this, it is necessary to evaluate whether ProtonMail continues to be a safe platform because technology is constantly advancing, and new dangers are continually emerging. Now, the question is, Is ProtonMail still secure? We will analyze ProtonMail’s encryption techniques, security features, and recent improvements to provide consumers with an up-to-date study of its safety record in this ProtonMail review.
The end-to-end encryption that ProtonMail provides and the company’s dedication to protecting user privacy helped the company gain popularity. Despite this, it is necessary to evaluate whether ProtonMail continues to be a safe platform because technology is constantly advancing, and new dangers are continually emerging. Now, the question is, Is ProtonMail still secure? We will analyze ProtonMail’s encryption techniques, security features, and recent improvements to provide consumers with an up-to-date study of its safety record in this ProtonMail review.
What is Proton Mail?
ProtonMail is an email service that prioritizes user security and privacy while encrypting messages. A team of researchers from MIT and CERN founded the email service ProtonMail in 2014. Only the sender and the recipient of an email can see its contents since it offers end-to-end encryption. Because of the encryption employed, ProtonMail cannot read or intercept the delivered messages.
The service aims to safeguard private data and thwart unauthorized access. As a result, it provides both individuals and corporations with a safe platform for email communications. ProtonMail has gained popularity as a reliable email provider for people who seek more privacy in a digital environment that is growing more surveillance-oriented. One of the critical factors in its success is the combination of its user-friendly interface and robust security features.
How does ProtonMail work?
End-to-end encryption is the foundation of ProtonMail’s operation, which safeguards the content of emails during their entire journey, from the sender to the recipient. Once a user sends an email to another user, the message undergoes instant encryption utilizing the recipient’s public key. This ensures that only the recipient to whom the message was sent may decrypt and access it. The operations of encrypting and decrypting communications occur on the devices associated with the users, with ProtonMail acting as a secure intermediary for transmitting encrypted messages. ProtonMail encrypts user data with powerful algorithms, preventing illegal access and offering high privacy and security for email communications.
ProtonMail assures that email exchanges are kept private and are shielded from illegal access by combining robust encryption, secure transmission, and user control over encryption keys.
Proton Mail: Pros and Cons
It is essential to weigh the benefits of using ProtonMail against its drawbacks before deciding whether or not it is the most suitable email provider for your requirements.
Pros:
- ProtonMail employs strong end-to-end encryption, guaranteeing that only authorized recipients can decrypt and access email content.
- ProtonMail firmly focuses on protecting users’ privacy. They are in Switzerland, which has tight privacy rules, and do not log IP addresses or monitor user behavior.
- ProtonMail has a simple, user-friendly interface accessible to people of all technological backgrounds.
- iOS and Android users can access ProtonMail through specialized mobile apps or web browsers. Due to their adaptability, users can easily access their encrypted email accounts on various devices.
- ProtonMail offers two-factor authentication, which gives user accounts additional protection.
Cons:
- ProtonMail does not provide broad integration with third-party apps or services because it focuses on security.
- The free tier of ProtonMail gives a small amount of storage, and the pricier subscriptions also have storage restrictions.
- Although ProtonMail provides secure communication within its platform, it can be more challenging to communicate securely with non-ProtonMail users.
- ProtonMail has a free plan, but some of its more sophisticated features and larger storage space require a premium plan membership.
- ProtonMail emails may occasionally experience deliverability problems or be marked as suspicious by specific email providers or filters due to their robust encryption and emphasis on privacy.
Is Proton Mail Still Secure?
Many people widely acknowledge that ProtonMail provides a secure email service. Robust end-to-end encryption is used, which encrypts emails on the sender’s device and allows only the intended receiver to decrypt them using their private key. ProtonMail cannot view the contents of user emails because of this. Furthermore, the Swiss jurisdiction governs ProtonMail, known for its stringent privacy rules and further enhances the security of user data.
However, it is essential to remember that the security landscape constantly shifts, and new vulnerabilities or threats may emerge over time. ProtonMail highly suggests that you stay current with the most recent information and security procedures to maintain your account’s level of protection.
Proton Mail’s Security Features
ProtonMail provides several security safeguards to ensure the privacy and security of user emails. ProtonMail offers the following security features:
1. End-to-End Encryption
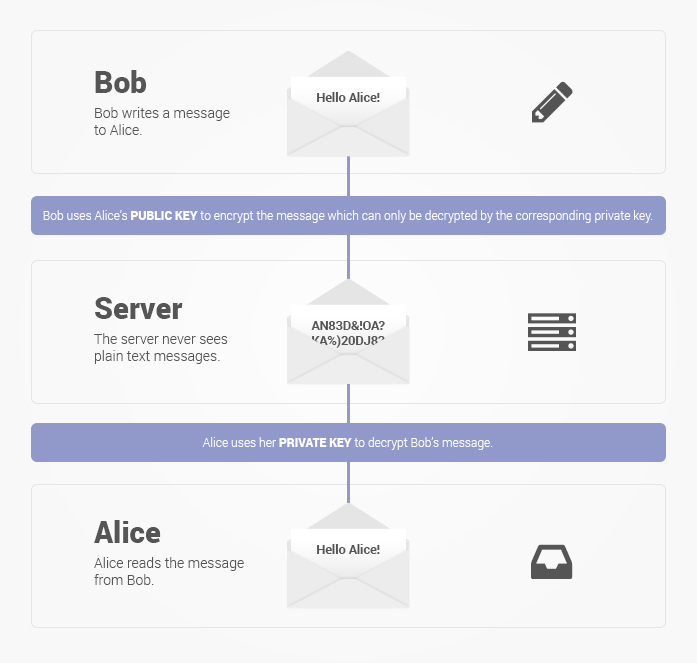
End-to-end encryption is the method that ProtonMail employs to protect the confidentiality and safety of its users’ email communications. The end-to-end encryption features encrypt the contents of emails on the sender’s device by using the receiver’s public key. The recipient who was supposed to receive it and possesses the appropriate private key ensures that only they can decrypt and access the message. This encryption occurs locally before the transmission, protecting the email from being intercepted or accessed by unauthorized parties.
Because ProtonMail does not have access to the decryption keys, it can guarantee that user data will remain secure and unavailable even to the service provider. Because this comprehensive encryption technology ensures that only the sender and the receiver have access to the content, ProtonMail is a safe and secure platform for conducting confidential communication.
2. Open Source Cryptography
ProtonMail’s use of open-source cryptography demonstrates its dedication to security and openness. The ProtonMail encryption methods and protocols are open-source, making them accessible to the general public for review and examination. ProtonMail enables security professionals and the general public to evaluate the potency and integrity of their encryption techniques by making their cryptography open source. Any possible weaknesses or vulnerabilities can be quickly detected and fixed through increased openness.
Additionally, open-source encryption avoids undetected flaws or hidden backdoors that can jeopardize the security of user data. The commitment of ProtonMail to open-source cryptography demonstrates its desire to offer consumers who seek email privacy and data protection a safe and reliable platform.
3. Forward Secrecy
The notion of forward Secrecy is incorporated into ProtonMail to increase the protection afforded to users’ communications. Forward Secrecy, also known as perfect forward Secrecy (PFS), assures that even if an encryption key is stolen in the future, it cannot be used to decrypt encrypted communications sent in the past. Another name for forward Secrecy is perfect forward Secrecy (PFS). In the context of ProtonMail, “forward secrecy” means that ProtonMail provides every email interaction between users with a unique session key that ProtonMail generates specifically for that session. We use this session key to encrypt and decrypt the communications and throw away the key once the session concludes.
4. Self-Destructing Emails
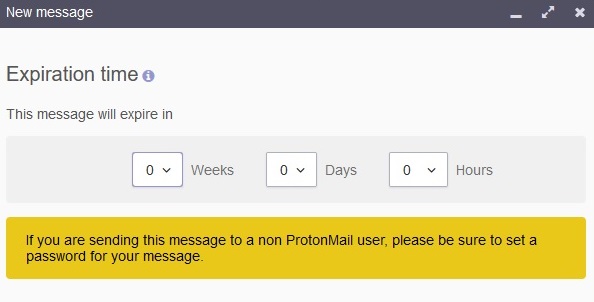
You can easily send an email message that deletes itself after it’s been read using ProtonMail for Android or iPhone, and you can send these messages to anyone, not just other ProtonMail users. It is possible to send a time-sensitive email to any email address; the service that sends the email must provide end-to-end encryption. The communications you send to those not using ProtonMail aren’t encrypted end-to-end by default, but changing this setting is challenging.
5. Two-Factor Authentication (2FA)
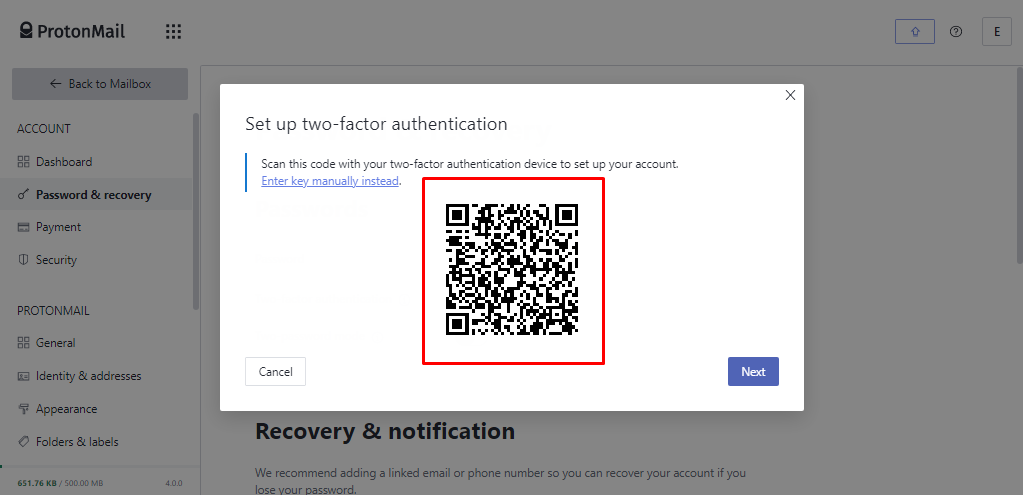
Two-Factor Authentication, or 2FA, is an additional security measure ProtonMail provides to protect your email account further. To log in using a Two-Factor Authentication system, you will need to give a second form of verification in addition to your password. This will add a step to the process.
You must submit a verification code when you set up two-factor authentication on your ProtonMail account. This code can be created by an authentication app on your mobile device or received via SMS. This code, in addition to your password, is necessary to access your account. ProtonMail helps ensure that even if someone can gain your password, they cannot access your account without the second factor by requiring this additional verification step. This helps protect your account from being hacked.
6. Anonymous Account Creation
Users can create anonymous accounts on ProtonMail, which offers an additional degree of protection for users who place a high priority on their anonymity. ProtonMail users do not need to enter personally identifying information (such as their name, phone number, or address) to create an account with ProtonMail. Users that prefer to maintain their anonymity benefit from this technique because it helps preserve their identity and privacy.
Simply going to the ProtonMail website and following the on-screen instructions to register an account is all required to use the service anonymously. You will get a prompt to select a username and password for your account while going through this procedure. You are free to choose any accessible username, and it is not required to be connected to your real name or any other personal information about you.
7. Tor Access
Users can increase their privacy and anonymity while accessing their email accounts with ProtonMail because the service enables access over the Tor network. Tor, often known as “The Onion Router,” is a network that hides the origin and destination of internet traffic by sending it through several relays. Determining where the communication originated and where it heads is more challenging.
Your internet traffic is encrypted and routed through a network of relays when you visit ProtonMail over Tor. Third parties find monitoring your online activities or determining your physical location more challenging.
Follow these instructions to use ProtonMail through Tor:
- Install Tor: Download the Tor Browser, a customized Firefox browser that works with Tor. It’s available through Tor Project.
- Connect to the Tor network: Launch Tor Browser and follow the directions to connect to Tor. The Tor Browser anonymizes your online actions by securely clicking on the Tor network.
- Access ProtonMail: Enter https://protonmail.com into the Tor Browser’s address bar and press Enter to access ProtonMail. This loads ProtonMail via Tor.
8. Phishing Protection
ProtonMail protects its users from phishing attacks by incorporating several measures. Phishing attacks are malicious attempts to deceive individuals into revealing sensitive information such as passwords, credit card details, or personal information.
ProtonMail uses anti-phishing mechanisms to detect and flag potential phishing emails. The user interface displays these warnings, alerting users about suspicious or potentially dangerous emails that may try to trick them into disclosing sensitive data.
ProtonMail actively educates and raises awareness among users about phishing attacks. Their website and support channels provide information and resources to help users recognize and avoid falling victim to phishing attempts. This includes guidance on identifying suspicious emails, avoiding clicking on suspicious links, and staying vigilant when sharing sensitive information.
Other Features of Proton Mail
Here are some additional features offered by ProtonMail:
- Password-Protected Emails: ProtonMail lets you password-protect your emails. Password-protected emails require a password to open.
- Email Filters and Sorting: ProtonMail lets you set rules to automatically sort, label, or act on incoming emails based on sender, subject, keywords, or other criteria.
- Cross-Platform Accessibility: ProtonMail has web, iOS, and Android apps. This offers secure and convenient email access across devices.
- Encrypted Attachments: ProtonMail encrypts email content and attachments. This protects files during email transmission and storage.
- Whitelisting and blacklisting: ProtonMail lets you choose whether senders’ emails are automatically filtered as spam or delivered to your mailbox.
- Autoresponder: ProtonMail’s autoresponder lets you automatically reply to emails. This helps senders get a response when you’re away.
Our Final Verdict: Is ProtonMail still secure?
Many people widely acknowledge that ProtonMail provides a secure email service. It combines several features and safeguards to preserve user privacy and data security, such as end-to-end encryption, open-source cryptography, self-destructing emails, two-factor authentication, and anonymous account creation. Other safeguards that are pretty good include self-destructing emails and self-destructing attachments in emails.
ProtonMail accounts further improve security by offering features such as phishing protection, two-factor authentication, and self-destructing emails. Users can also keep a higher level of privacy and anonymity thanks to the fact that ProtonMail allows for establishing anonymous accounts and provides access to the Tor network.
On the contrary, it is essential to remember that the security landscape constantly shifts and that new holes in protection or dangers may appear over time. ProtonMail highly suggests that you stay updated with the most recent information and security procedures they provide to maintain your account’s level of protection.





